Introduction
In today’s rapidly evolving threat landscape, security teams must act fast—every second counts. Traditional incident response workflows are often siloed, manual, and time-consuming, leaving teams overwhelmed and vulnerable to breaches.
Cyware Respond was designed to solve this challenge by offering a next-gen Security Orchestration, Automation, and Response (SOAR) platform. The goal: to empower SOC teams with real-time visibility, collaborative response capabilities, and intelligent automation across the threat lifecycle.
As UX researcher, my mission was to deeply understand how security analysts work under pressure and how we could transform their fragmented experiences into a unified, intuitive, and responsive system. This case study explores our journey—through stakeholder interviews, field studies, and iterative testing—to build a design that supports rapid, coordinated, and intelligent incident response.
The UX Behind the Shield
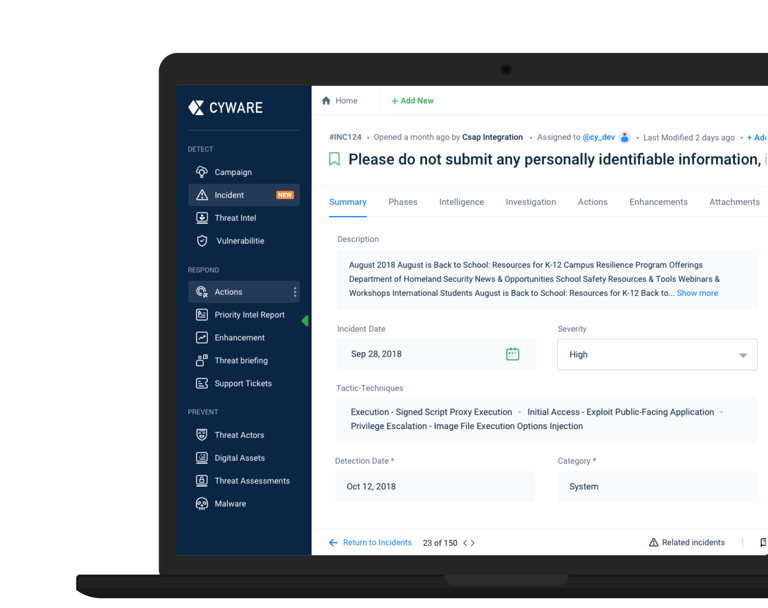
?
The Challenge
The current threat incident response application presented significant usability challenges. Analysts struggled with a convoluted and unintuitive interface, which led to delays in identifying threats, investigating incidents, and taking timely action. These inefficiencies not only increased response time but also increased the risk of security breaches.
Project Goals
Enhance detection and response efficiency: Streamlining the process to allow quicker,
more effective threat handling.
Foster better collaboration: Improve communication between team members during
investigations.
Minimize incident response time: Ensure analysts can act quickly by eliminating friction in
their workflows.
Create a user-centered design: Tailor the design to meet the unique needs and workflows
of security professionals.


"
Project Details
Total Duration
12 Weeks
Role
UX UI Design
Team Size
3 Members



01
User Interviews and Observations (6 Weeks)
To understand the users' needs, I conducted in-depth interviews and observation sessions with security analysts. The goal was to uncover their pain points, task flow, and desired improvements. I worked closely with analysts, gathering insights into how they interact with current systems, what features they find most useful, and where they face bottlenecks.
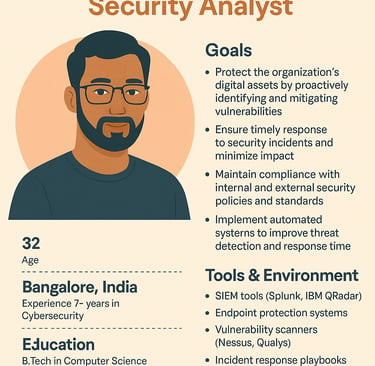
Persona Development:
Based on the interviews, two primary personas were developed:
02
Usability Testing (2 Weeks)
During the initial usability testing, I identified key pain points:
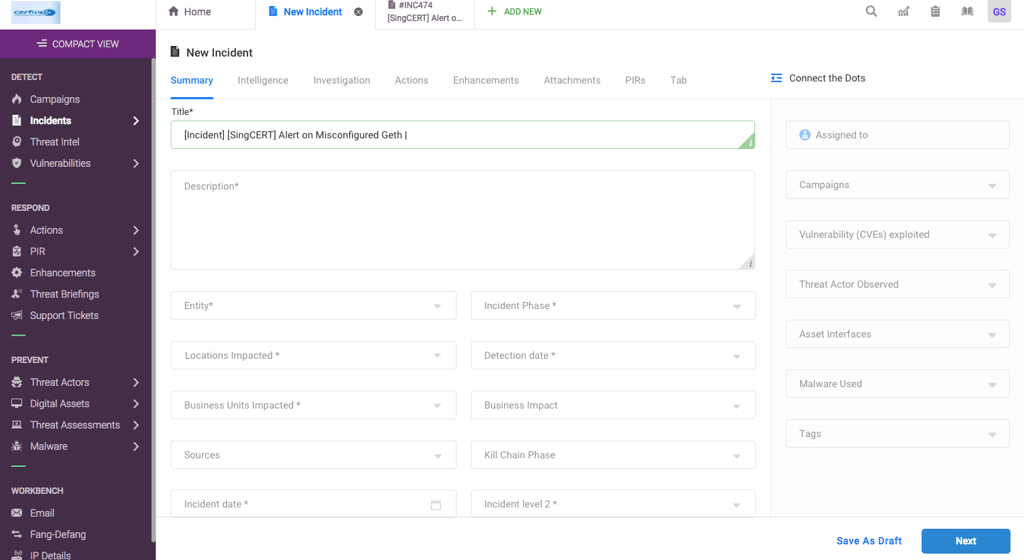
Issue 1: Lengthy Incident Submission Process
Problem: The process of submitting an incident was time-consuming and cumbersome.
Solution:
Simplify the incident submission form.
Provide options to customize the incident submission form.
Implement automated or prefilled information to expedite the process.
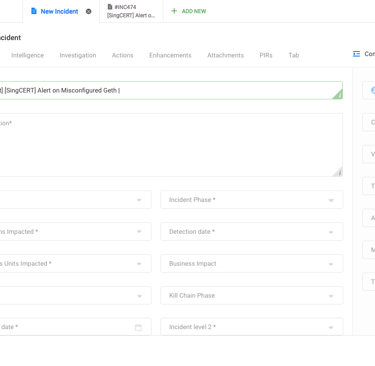
Issue 2: Inflexible Editing Capabilities
Problem: Users had to edit the entire incident to update specific information, leading to inefficiencies.
Solution:
Enable granular editing of incident details.
Introduce revision history to track changes.
Implement inline editing features.
Allow users to save drafts.
Provide clear notifications for changes made.
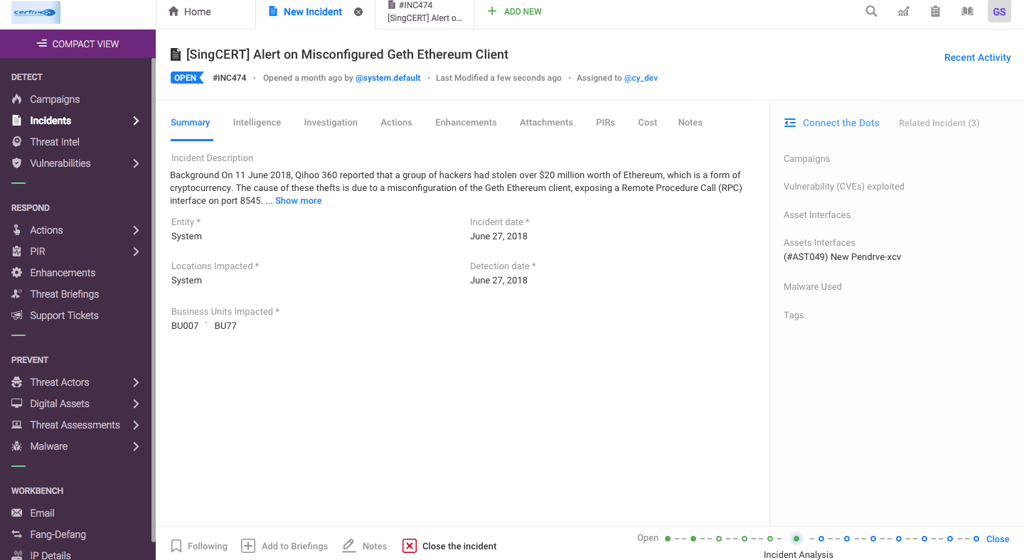
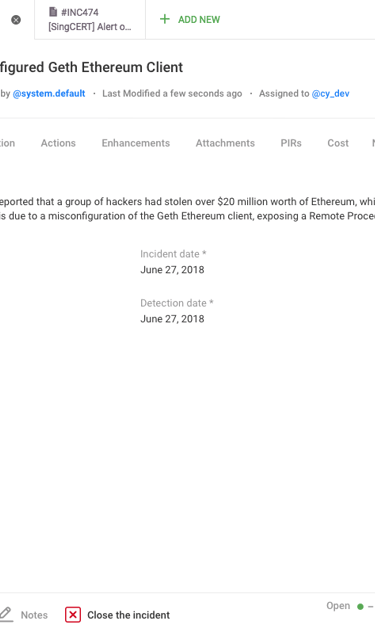
03
Design & Iteration (4 Weeks)
The design process was highly iterative, with quick feedback loops involving real security analysts. Each iteration provided new insights, helping me fine-tune the application’s user interface. For example, we introduced features like customizable incident forms and inline editing, which were directly informed by user feedback.
Implemented Solutions:
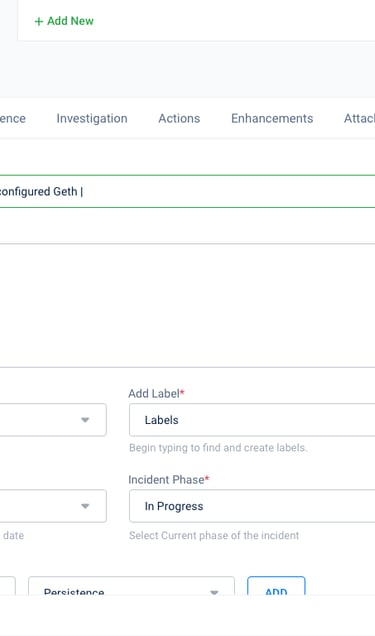
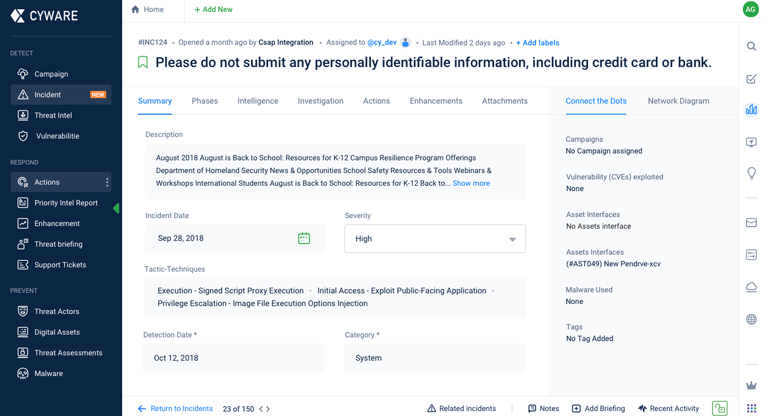
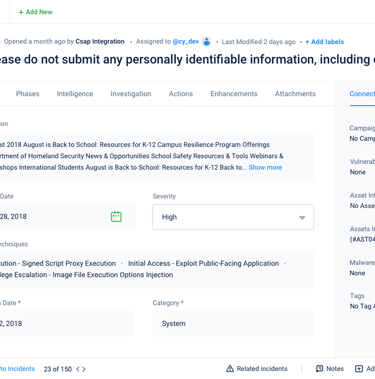
Simplified the incident form and details.
Allowed editing of specific information without modifying the entire incident.
Provided administrators with options to customize the incident form.
Introduced revision history, inline editing, and the ability to save drafts.
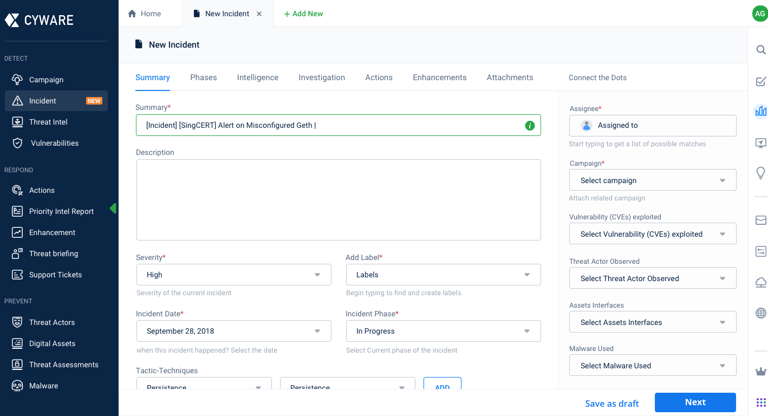
Roadblocks, Realizations & the Resolution


The most significant challenge was conducting in-depth user research within a corporate setting and making tough design decisions to prioritize a user-centric interface.
Through iterative design, constant feedback, and usability testing, we successfully revamped the application, leading to a significant improvement in the analysts' workflow.
The final design now supports rapid detection and resolution of security incidents, enhancing the organization's security posture.
