Introduction
We are working on building a powerful and reliable antivirus software that goes beyond basic protection. The goal is to offer advanced security features that safeguard users from a wide variety of cyber threats, including:
Viruses – malicious programs that can corrupt or steal data.
Spyware – software that secretly monitors user activity.
Ransomware – threats that lock your data and demand payment.
Phishing attacks – attempts to trick users into revealing sensitive information.
This antivirus solution will be versatile and scalable, designed to protect not just personal computers, but also servers and mobile devices. It aims to serve both individual users and businesses by delivering a comprehensive, all-in-one cybersecurity tool that continuously monitors, detects, and neutralizes threats in real-time.
McAfee: Where Privacy Meets Power
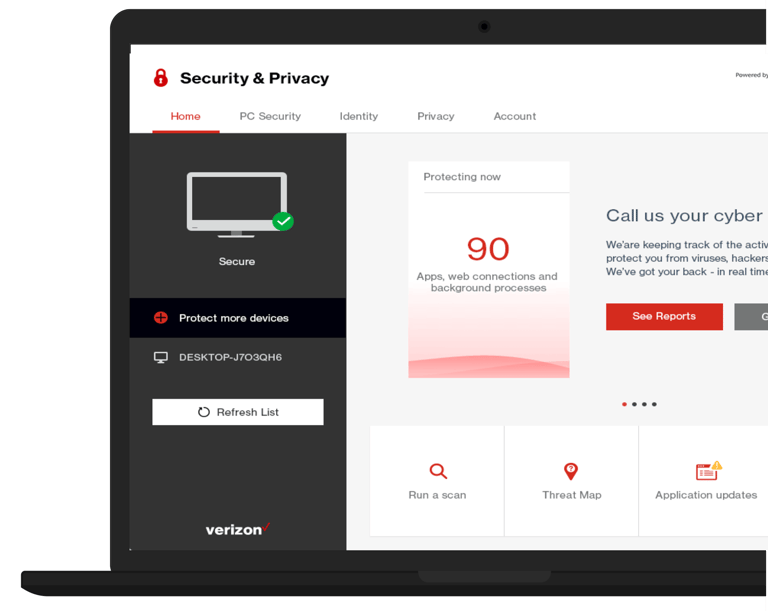
?
The Challenge
In today’s increasingly digital world, users face a growing number of sophisticated cybersecurity threats, from viruses and spyware to ransomware and phishing attacks. The challenge was to design an antivirus software solution that not only provides comprehensive, real-time protection against these diverse threats but also maintains a seamless and efficient user experience.
The goal was to develop a security tool that is powerful yet lightweight, ensuring system resources aren't drained or slowed down during operation. Additionally, the solution needed to cater to a broad user base, including individuals, small businesses, and enterprise-level clients, across platforms like Windows, macOS, Android, and iOS.


"
Project Details
Requirements Gathering
1 Week
Wireframes
2 Weeks
UI Design
2 Weeks
01
✅ Requirements Gathering
The requirements for an antivirus product may vary based on specific needs and contexts. However, here are some requirements which i got it from stack holder & product manager:
Malware Detection: Identify and block viruses, Trojans, ransomware, spyware, etc.
Real-Time Protection: Auto-detect threats instantly to prevent infections.
Frequent Updates: Keep virus definitions and engine current.
Customizable Scanning: Offer full and selective scan options with cleaning tools.
Behavioral Analysis: Detect suspicious activity even without known signatures.
Web & Email Security: Block malicious URLs, phishing, and harmful email attachments.
Firewall Support: Work with firewalls to prevent unauthorized access.
Low Resource Usage: Maintain system speed and performance.
User-Friendly UI: Simple dashboard for settings, scans, and reports.
Quarantine & Recovery: Isolate, restore, or delete threats safely.
Logs & Reporting: Detailed event tracking and history for audits.
Cross-Platform Support: Work across desktop, server, and mobile OS.
Privacy Focused: Secure data handling and transparent policies.
User Interviews
3 Weeks
Personas
1 Week
02
🎤 Listening First: User Interviews That Shaped the Experience
Before diving into pixels and prototypes, I set out to deeply understand real users — not just what they do, but why they do it. Over four focused days, I connected with 7 users remotely, all of whom actively use antivirus software in professional or personal settings.
To guide our conversations, I created a set of open-ended questions designed to unpack motivations, habits, pain points, and preferences — turning vague assumptions into clear insights.
🔍 Interview Objectives
Understand users’ daily interactions with antivirus tools
Identify key frustrations and unmet needs
Discover how users balance security vs. performance
Capture ideas for integrations, alerts, and UI clarity
💬 A Few Thought-Starters We Explored
“What frustrates you most when using antivirus tools?”
“How do you prefer to be alerted when threats are detected?”
“Can you walk me through how you run scans or manage updates?”
“What does ‘peace of mind’ look like in a security product for you?”
🎯 Outcome
The conversations were rich, raw, and revealing — leading to two refined personas and a clear picture of what an ideal antivirus experience should feel like: non-intrusive, powerful, intuitive, and always one step ahead.
These user voices echoed throughout the design process, helping us test assumptions and stay grounded in real-world needs.
03
🎭 Personas: Humanizing the Data
We wanted to form a deeper understanding of our users' goals, needs, experiences, and behaviors. So, we created 2 personas for each of our user segments. They were based on user interviews, and we kept updating them throughout the project as we gathered more data. We used these personas whenever we wanted to step out of ourselves and reconsider our initial ideas.




04
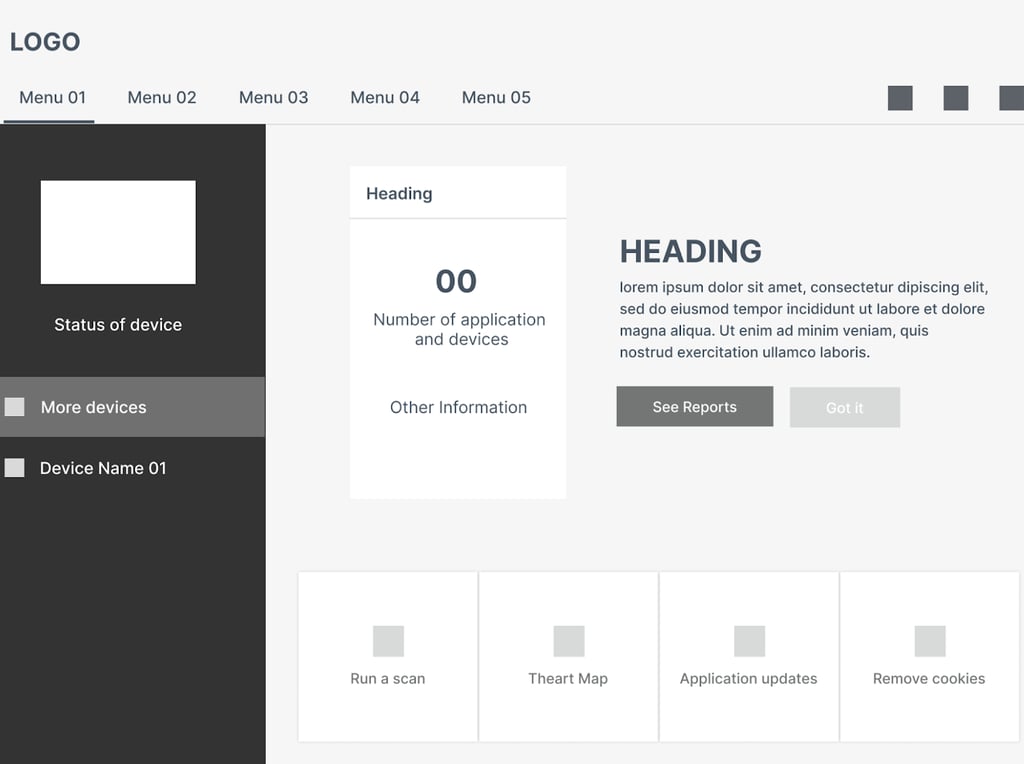
🧩 From Sketch to Screen: Crafting Ideas with Wireframes
Great design starts with asking “What if?” — and wireframes are where those ideas begin to breathe.
Using Figma, I translated rough pencil sketches into low-fidelity wireframes, allowing quick ideation and early feedback. These blueprints were intentionally minimal — just enough to map the user journey and explore interaction flows without getting distracted by visuals.
Once the structure felt right, I layered in marketing copy and real imagery, gradually evolving the frames into high-fidelity prototypes with pixel-level detail. This phase not only aligned visuals with business goals but also made testing more realistic.
05
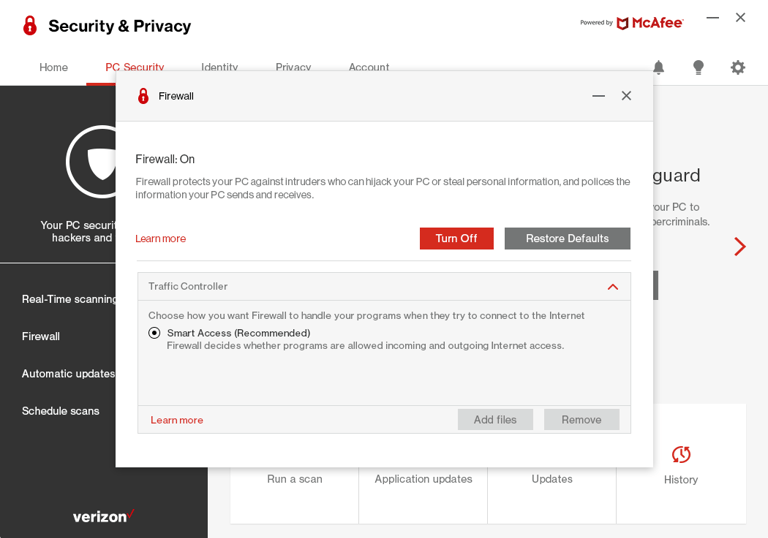
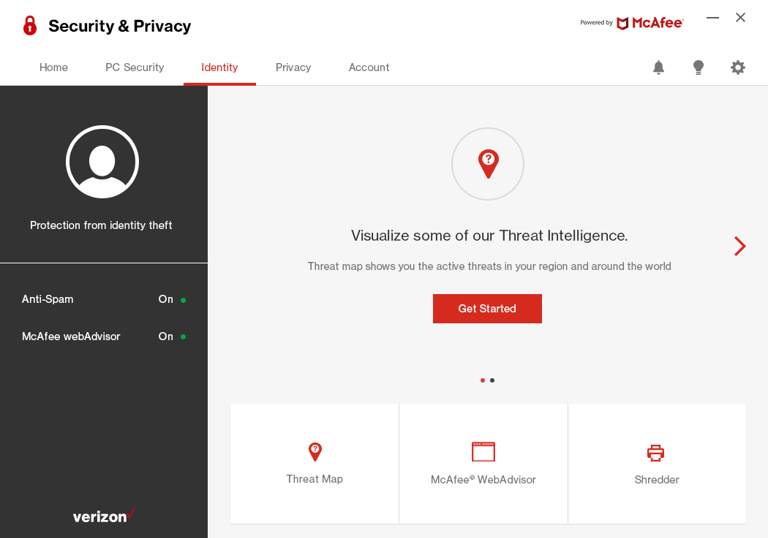
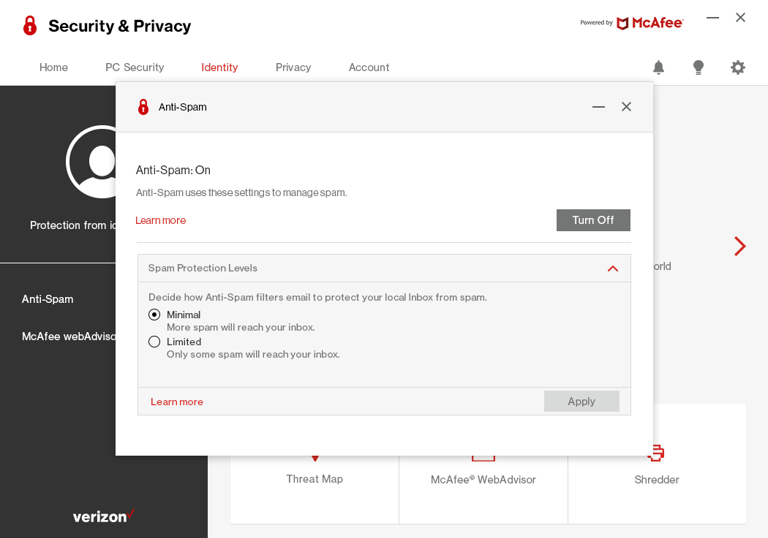
🎨 Solutions We Designed
Once the usability issues were resolved, I moved on to design the final screens in Figma. My goal was to create a visual identity that’s aligned with the design system. Also, I’ve checked the competition and took a deep dive into my catalog of references for inspiration.
I have used McAfee style guidelines (Light theme).
This design was for desktop application so ihave designed it

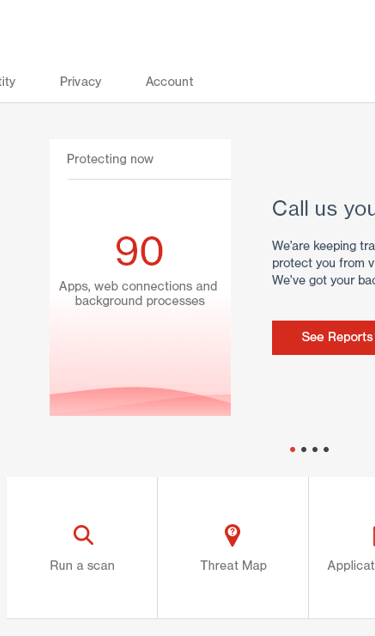
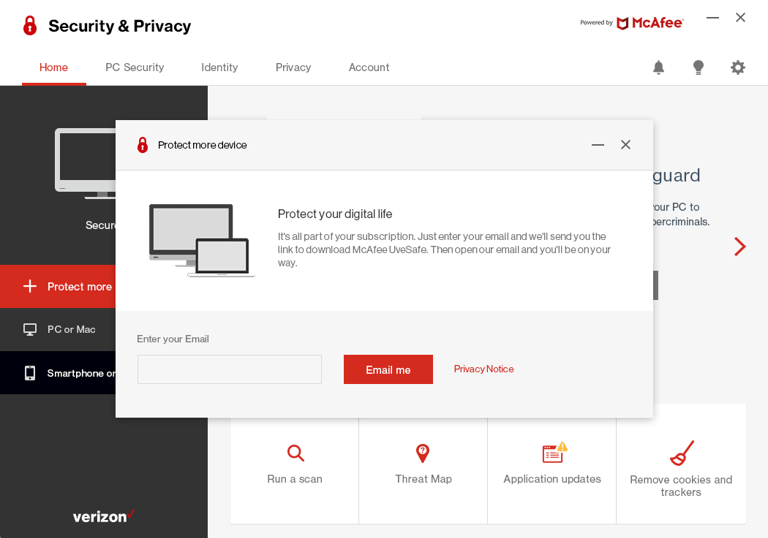
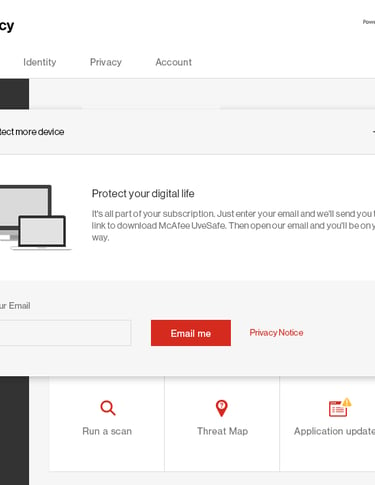

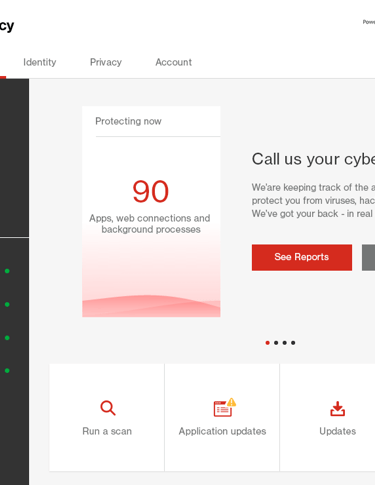
Conclusion
This project reinforced the critical role of trust and simplicity in cybersecurity experiences. By integrating user research, iterative design, and usability testing, we crafted a solution that balanced robust protection with user-friendly interaction. The outcome wasn’t just a more intuitive interface — it was a shift in perception, turning security tools from intimidating to empowering. Ultimately, we helped users feel more in control of their digital safety, without being overwhelmed by complexity.


